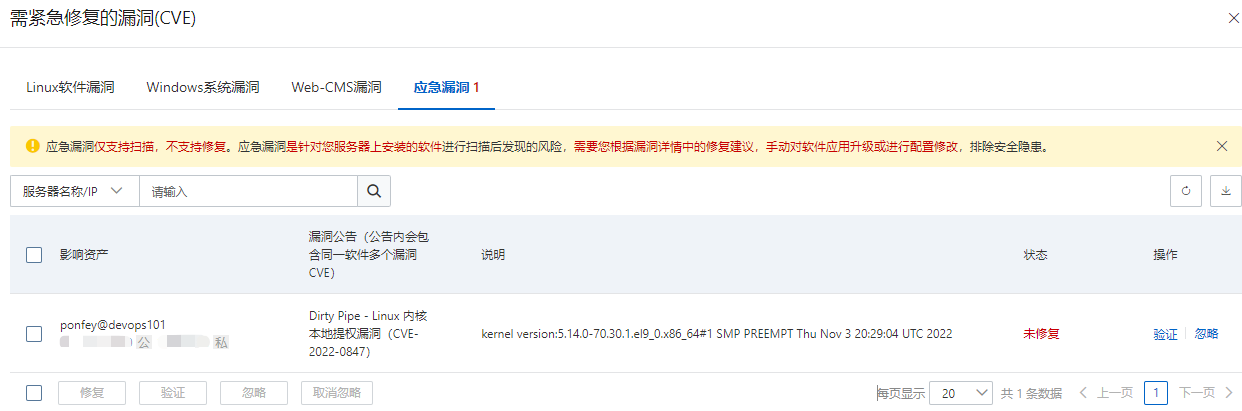
2021-09-01 21:03:09 星期三
OpenSSL拒绝服务漏洞(CVE-2020-1971)
响应办法:升级OpenSSL版本
[root@devops-rhel79-privatecloud-shanghai-area0 Packages]# wget https://www.openssl.org/source/openssl-1.1.1l.tar.gz # 下载最新版本OpenSSL(截至2021-09-01,发行版本为 openssl-1.1.1l released August 24, 2021)
[root@devops-rhel79-privatecloud-shanghai-area0 Packages]# cp openssl* /opt
[root@devops-rhel79-privatecloud-shanghai-area0 Packages]# cd /opt/
[root@devops-rhel79-privatecloud-shanghai-area0 opt]# tar -zxvf openssl-1.1.1l.tar.gz # 解压openssl-1.1.1l源码包
[root@devops-rhel79-privatecloud-shanghai-area0 opt]# cd openssl-1.1.1l/
[root@devops-rhel79-privatecloud-shanghai-area0 openssl-1.1.1l]# ./config --prefix=/usr/local/openssl # 编译前环境配置
[root@devops-rhel79-privatecloud-shanghai-area0 openssl-1.1.1l]# ./config -t # 编译前环境配置
[root@devops-rhel79-privatecloud-shanghai-area0 openssl-1.1.1l]# make # make 编译
[root@devops-rhel79-privatecloud-shanghai-area0 openssl-1.1.1l]# make install # make install 编译安装
[root@devops-rhel79-privatecloud-shanghai-area0 openssl-1.1.1l]# ldd /usr/local/openssl/bin/openssl # 检查函数库
[root@devops-rhel79-privatecloud-shanghai-area0 openssl-1.1.1l]# echo "/usr/local/openssl/lib" >>/etc/ld.so.conf # 添加所缺函数库
[root@devops-rhel79-privatecloud-shanghai-area0 openssl-1.1.1l]# ldconfig -v # 更新函数库
[root@devops-rhel79-privatecloud-shanghai-area0 openssl-1.1.1l]# mv /usr/bin/openssl /usr/bin/openssl_old_bak # 将旧版本openssl移除
[root@devops-rhel79-privatecloud-shanghai-area0 openssl-1.1.1l]# ln -s /usr/local/openssl/bin/openssl /usr/bin/openssl # 将新版本openssl软链接到/usr/bin/目录下
[root@devops-rhel79-privatecloud-shanghai-area0 openssl-1.1.1l]# which openssl #检查版本
[root@devops-rhel79-privatecloud-shanghai-area0 openssl-1.1.1l]# openssl version -aOpenSSH 命令注入漏洞(CVE-2020-15778)
OpenSSH(OpenBSD Secure Shell)是OpenBSD计划组的一套用于安全访问远程计算机的连接工具。该工具是SSH协议的开源实现,支持对所有的传输进行加密,可有效阻止窃听、连接劫持以及其他网络级的攻击。
OpenSSH 8.4p1及之前版本中的scp的scp.c文件存在命令注入漏洞。该漏洞源于外部输入数据构造可执行命令过程中,网络系统或产品未正确过滤其中的特殊元素,攻击者可利用该漏洞执行非法命令。
响应办法:
目前厂商暂未发布修复措施解决此安全问题,这里选择对OpenSSH进行版本升级。
环境准备:(内网环境需部署本地光盘镜像源)
准备升级包 zlib-1.2.11.tar.gz、openssl-1.1.1l.tar.gz、openssh-8.6p1.tar.gz
[root@devops-rhel79-privatecloud-shanghai-area0 Packages]# yum install telnet-server.x86_64 telnet.x86_64 xinetd -y # 安装并临时启用telnet,全程使用telnet对OpenSSH版本进行升级、验证
[root@devops-rhel79-privatecloud-shanghai-area0 Packages]# cp /etc/securetty /etc/securetty.bak
[root@devops-rhel79-privatecloud-shanghai-area0 Packages]# echo "pts/0" >> /etc/securetty
[root@devops-rhel79-privatecloud-shanghai-area0 Packages]# echo "pts/1" >> /etc/securetty
[root@devops-rhel79-privatecloud-shanghai-area0 Packages]# echo "pts/2" >> /etc/securetty
[root@devops-rhel79-privatecloud-shanghai-area0 Packages]# echo "pts/3" >> /etc/securetty
[root@devops-rhel79-privatecloud-shanghai-area0 Packages]# systemctl restart telnet.socket && systemctl restart xinetd
[root@devops-rhel79-privatecloud-shanghai-area0 Packages]# systemctl enable telnet.socket && systemctl enable xinetd
[root@devops-rhel79-privatecloud-shanghai-area0 Packages]# systemctl stop sshd # 停止SSH服务,保留窗口,另行开一个telnet窗口进行操作
**先进行对 OpenSSL拒绝服务漏洞(CVE-2020-1971)升级,再进行OpenSSH升级。**
[root@devops-rhel79-privatecloud-shanghai-area0 Packages]# wget https://cdn.openbsd.org/pub/OpenBSD/OpenSSH/portable/openssh-8.6p1.tar.gz 下载指定版本OpenSSH(截至2021-09-01,发行版本为 OpenSSH 8.7 released August 20, 2021,考虑安全稳定性暂不升级至最新版本)
[root@devops-rhel79-privatecloud-shanghai-area0 Packages]# cp openssh* /opt
[root@devops-rhel79-privatecloud-shanghai-area0 opt]# yum -y install zlib-devel
[root@devops-rhel79-privatecloud-shanghai-area0 opt]# yum -y install pam-devel
[root@devops-rhel79-privatecloud-shanghai-area0 opt]# tar -zxvf openssh-8.6p1.tar.gz # 解压openssh-8.6p1源码包
[root@devops-rhel79-privatecloud-shanghai-area0 opt]# cd openssh-8.6p1/
[root@devops-rhel79-privatecloud-shanghai-area0 openssh-8.6p1]# mv /etc/ssh /etc/ssh_bak # 备份旧版本
[root@devops-rhel79-privatecloud-shanghai-area0 openssh-8.6p1]# ./configure --prefix=/usr/local/openssh --sysconfdir=/etc/ssh --with-pam --with-ssl-dir=/usr/local/openssl --with-md5-passwords --mandir=/usr/share/man --with-zlib=/usr/local/zlib --without-hardening # 编译前环境配置
[root@devops-rhel79-privatecloud-shanghai-area0 openssh-8.6p1]# make # make编译
[root@devops-rhel79-privatecloud-shanghai-area0 openssh-8.6p1]# make install # make install 编译安装
[root@devops-rhel79-privatecloud-shanghai-area0 openssh-8.6p1]# echo "PermitRootLogin yes" >> /etc/ssh/sshd_config # 修改/etc/ssh/sshd_config配置,允许root用户SSH登录,openssh-8.6p1配置中无此选项
[root@devops-rhel79-privatecloud-shanghai-area0 openssh-8.6p1]# mv /usr/sbin/sshd /usr/sbin/sshd_bak #备份旧版本sshd
[root@devops-rhel79-privatecloud-shanghai-area0 openssh-8.6p1]# mv /etc/sysconfig/sshd /opt
[root@devops-rhel79-privatecloud-shanghai-area0 openssh-8.6p1]# mv /usr/lib/systemd/system/sshd.service /opt
[root@devops-rhel79-privatecloud-shanghai-area0 openssh-8.6p1]# cp -arf /usr/local/openssh/sbin/sshd /usr/sbin/sshd # 拷贝新版本sshd到/usr/sbin/
[root@devops-rhel79-privatecloud-shanghai-area0 openssh-8.6p1]# for i in $(rpm -qa |grep openssh);do rpm -e $i --nodeps ;done # 卸载原有openssh
[root@devops-rhel79-privatecloud-shanghai-area0 openssh-8.6p1]# mv /etc/ssh/sshd_config.rpmsave /etc/ssh/sshd_config # 卸载后openssh配置文件会变成rpmsave后缀,还原到原来目录下
[root@devops-rhel79-privatecloud-shanghai-area0 openssh-8.6p1]# mv /etc/ssh/ssh_config.rpmsave /etc/ssh/ssh_config
[root@devops-rhel79-privatecloud-shanghai-area0 openssh-8.6p1]# mv /etc/ssh/moduli.rpmsave /etc/ssh/moduli
[root@devops-rhel79-privatecloud-shanghai-area0 openssh-8.6p1]# cp -arf /usr/local/openssh/bin/* /usr/bin/ # 替换新版本openssh相关命令
[root@devops-rhel79-privatecloud-shanghai-area0 openssh-8.6p1]# cp -arf /usr/local/openssh/sbin/sshd /usr/sbin/sshd
[root@devops-rhel79-privatecloud-shanghai-area0 openssh-8.6p1]# cp /opt/openssh-8.6p1/contrib/redhat/sshd.init /etc/init.d/sshd # 拷贝启动脚本
[root@devops-rhel79-privatecloud-shanghai-area0 openssh-8.6p1]# chmod +x /etc/init.d/sshd # 给启动脚本添加执行权限
[root@devops-rhel79-privatecloud-shanghai-area0 openssh-8.6p1]# cp -a contrib/redhat/sshd.pam /etc/pam.d/sshd.pam # 拷贝sshd.pam
[root@devops-rhel79-privatecloud-shanghai-area0 openssh-8.6p1]# systemctl daemon-reload #重启sshd服务并设为开机自启动
[root@devops-rhel79-privatecloud-shanghai-area0 openssh-8.6p1]# systemctl restart sshd
[root@devops-rhel79-privatecloud-shanghai-area0 openssh-8.6p1]# chkconfig --add sshd
[root@devops-rhel79-privatecloud-shanghai-area0 openssh-8.6p1]# chkconfig --level 2345 sshd on
[root@devops-rhel79-privatecloud-shanghai-area0 openssh-8.6p1]# chkconfig --list
[root@devops-rhel79-privatecloud-shanghai-area0 ~]# ssh -V # 需要注意,前面是包含卸载openssh-clients
OpenSSH_8.6p1, OpenSSL 1.1.1l 24 Aug 2021
[root@devops-rhel79-privatecloud-shanghai-area0 ~]# yum install -y openssh-clients # 如后续使用ssh-copy-id等功能的,需安装openssh-clients
[root@devops-rhel79-privatecloud-shanghai-area0 ~]# ssh -V # 这里查看的是ssh client的版本信息
OpenSSH_7.4p1, OpenSSL 1.0.2k-fips 26 Jan 2017
[root@devops-rhel79-privatecloud-shanghai-area0 ~]# sshd -V # 这里查看的是ssh server的版本信息
unknown option -- V
OpenSSH_8.6p1, OpenSSL 1.1.1l 24 Aug 2021
usage: sshd [-46DdeiqTt] [-C connection_spec] [-c host_cert_file]
[-E log_file] [-f config_file] [-g login_grace_time]
[-h host_key_file] [-o option] [-p port] [-u len]Sudo 本地权限提升高危漏洞(CVE-2021-3156)
响应办法:升级sudo版本
1)CentOS 6:默认 sudo 在受影响范围,CentOS官方已停止更新。
2)CentOS 7:升级到 sudo-1.8.23-10.el7_9.1 或更高版本 # $ yum update sudo
3)CentOS 8:升级到 sudo-1.8.29-6.el8_3.1或更高版本
自查方法:
1、以非root账户登录系统运行如下命令:
[root@devops-rhel79-privatecloud-shanghai-area0 Packages]# sudoedit -s /2、若受影响,错误信息会以如下内容开头:
[root@devops-rhel79-privatecloud-shanghai-area0 Packages]# sudoedit: /: not a regular file3、若已安装补丁,错误信息会以如下内容开头:
usage: sudoedit [-AknS] [-r role] [-t type] [-C num] [-g group] [-h host] [-p prompt] [-T timeout] [-u user] file ...